The IoT Chain is a fusion of the Internet of Things theory and blockchain technology, and is committed to building a big data blockchain with the Internet of Everything. The traditional IoT operating platform uses centralized technology. Regardless of data collection or operation, any party participating in the IoT is a prerequisite for due diligence. The slow development of the trust mechanism has seriously hindered the development of the IoT market. . In response to the problems that arise in the process of the Internet of Things, the IoT chain focuses on the data acquisition, data concurrency, and data coexistence problems faced by the application of blockchain technology to the Internet of Things industry, and combines the blockchain-Internet of Things-big data to build a new generation IoT system architecture.
The IoT chain stores the data of the IoT participants in each link to realize the conversion of assets. At the same time, the material chain has established a technology-based trust system for basic data with the help of the characteristics of the blockchain. In the material chain, due to its immutability and traceability, participants have absolute trust in the fairness of the transaction mechanism, which guarantees the normal operation of the transaction.
The material chain and blockchain technology are highly coupled1 Object number chain
The purpose of the thing number chain is to integrate and improve the concept of on-chain meta-protocol, scripts, smart contracts, cross-chain collaboration, and distributed storage, so that developers can create arbitrary consensus-based, An extended, standardized, fully-featured, easy-to-develop and collaborative data display and data storage platform. By establishing the ultimate abstract base layer-a blockchain with Turing complete programming language built-in-anyone can create contracts and decentralized applications, and set up their freely defined ownership rules, transaction methods and state transitions. function.
2 Material Chain Account
In the account system, the state is composed of objects called "accounts" (each account consists of a 20-byte address) and state transitions that transfer value and information between the two accounts. The LDBC account consists of four parts:
• A random number, a counter used to determine that each transaction can only be processed once
• The current balance of the account
• The contract code of the account
• Account storage (empty by default)
LDBC is the main encrypted fuel inside the material chain, used to pay transaction fees. Generally speaking, there are two types of accounts: externally owned accounts (controlled by private keys) and contract accounts (controlled by contract codes).
All external accounts have no code, and people can send messages from an external account by creating and signing a transaction. Whenever the contract account receives a message, the code inside the contract will be activated, allowing it to read and write to the internal storage, and send other messages or create a contract.
3 News and transactions
First, messages can be created by external entities or contracts, but Bitcoin transactions can only be created externally. Second, the message can optionally contain data. Third, if the recipient of the message is a contract account, you can choose to respond, which means that the message of the number chain also contains the concept of function.
The "transaction" in the material chain refers to the signature data packet that stores the message sent from the external account. The transaction includes the recipient of the message, the signature used to confirm the sender, the currency account balance, the data to be sent, and two values ​​called STARTGAS and GASPRICE. In order to prevent the exponential explosion and infinite loop of the code, each transaction needs to limit the calculation steps caused by the execution of the code-including the initial message and all messages triggered during the execution. STARTGAS is the limit, and GASPRICE is the cost of the miner that needs to be paid for each calculation step. If in the process of executing the transaction, "fuel is used up", all state changes will be restored to the original state, but the transaction fees that have been paid cannot be recovered. If there is fuel remaining when the transaction is executed, the fuel will be returned to the sender. There are separate transaction types and corresponding message types to create a contract; the address of the contract is calculated based on the account random number and the hash of the transaction data.
An important consequence of the message mechanism is the "first class citizen" property of the material chain-contracts have the same rights as external accounts, including the right to send messages and create other contracts. This allows the contract to play multiple different roles at the same time. For example, a user can make a member of a decentralized organization (a contract) become an intermediary account (another contract), for a paranoid use of a customized quantum proof-based LAN The individual of Porter's signature (the third contract) and a co-signing entity that uses an account secured by five private keys (the fourth contract) provides intermediary services. The material chain does not need to care about what type of account each participant of the contract is.
4 The state transition function of the number chain
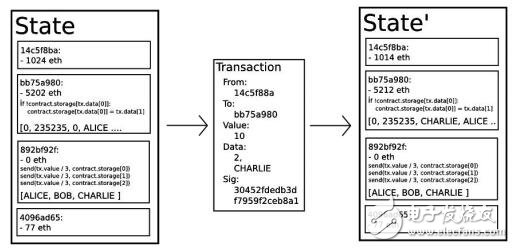
The state transition function of the material number chain: APPLY (S, TX)-"S', which can be defined as follows:
1 Check whether the format of the transaction is correct (that is, it has the correct value), whether the signature is valid and whether the random number matches the random number of the sender's account. If not, return an error.
2 Calculate the transaction fee: fee=STARTGAS * GASPRICE, and determine the sender's address from the signature. Subtract the transaction fee from the sender’s account and increase the sender’s random number. If the account balance is insufficient, an error is returned.
3 Set the initial value GAS = STARTGAS, and subtract a certain amount of fuel value according to the number of bytes in the transaction.
4 Transfer value from the sender's account to the receiver's account. If the receiving account does not exist yet, create this account. If the receiving account is a contract, run the code of the contract until the code runs out or the fuel runs out.
5 If the value transfer fails because the sender's account does not have enough money or the code execution runs out of fuel, the original state is restored, but the transaction fee is still required, and the transaction fee is added to the miner's account.
6 Otherwise, return all the remaining fuel to the sender, and send the consumed fuel to the miner as a transaction fee.
For example, suppose the code of the contract is as follows:
if! contract.storage[msg.data[0]]:
contract.storage[msg.data[0]] = msg.data[1]
It should be noted that in reality, the contract code is written in the underlying virtual machine code. Assuming that the contract memory is empty at the beginning, one value is 10 coins, fuel is 2000, fuel price is 0.001 coins and two data field values ​​are [2,'CHARLIE'] [3]. After the transaction is sent, the state changes The processing process of the function is as follows:
1 Check whether the transaction is valid and the format is correct.
2 Check that the sender of the transaction has at least 2000*0.001=2 coins. If so, subtract 2 coins from the sender's account.
3 Initially set gas=2000. Assuming that the transaction length is 170 bytes, the cost per byte is 5, minus 850, so there is 1150 left.
4 Subtract 10 coins from the sender's account and add 10 coins to the contract account.
5 Run the code. In this contract, the running code is very simple: it checks whether the contract memory index is 2 is used, notices that it is not used, and then sets its value to CHARLIE. Suppose this consumes 187 units of fuel, so the remaining fuel is 1150 – 187 = 963.
6. Add 963*0.001=0.963 coins to the sender's account and return to the final state.
If there is no contract to accept the transaction, then all transaction fees are equal to GASPRICE multiplied by the byte length of the transaction, and the transaction data has nothing to do with transaction fees. In addition, it should be noted that the messages initiated by the contract can allocate a fuel limit to the calculations they generate. If the fuel of the sub-calculation runs out, it will only restore to the state when the message was sent. Therefore, just like transactions, contracts can also protect their computing resources by setting strict limits on the sub-computations it generates.
5 Code execution
The code of the material number chain contract is written in a low-level stack-based bytecode language and is called the "material number chain virtual machine code". The code consists of a series of bytes, each of which represents an operation. Generally speaking, code execution is an infinite loop, and an operation is executed every time the program counter increases by one (the initial value is zero), until the code execution is completed or an error is encountered, STOP or RETURN instructions. Operations can access three types of data storage spaces:
â—Stack, a last-in, first-out data storage, 32-byte values ​​can be pushed into the stack and popped out of the stack.
â—Memory, infinitely expandable byte queue.
â—Long-term storage of contracts, a storage of secret keys/values, where both the secret key and the value are 32 bytes in size. Unlike the stack and memory that are reset at the end of the calculation, the storage content will be kept for a long time.
The code can access the value like the block header data, the data in the sender and the received message, and the code can also return the byte queue of the data as output.
The formal execution model of virtual machine code is surprisingly simple. When the material chain virtual machine is running, its complete calculation state can be defined by tuples (block_state, transaction, message, code, memory, stack, pc, gas), where block_state is the global account that contains all account balances and storage status. In each round of execution, by calling the pc (program counter) byte of the code, the current instruction is found, and each instruction has its own definition of how to affect the tuple. For example, ADD pops two elements from the stack and pushes their sum to the stack, subtracts one from gas (fuel) and adds one to pc, SSTORE pops the top two elements from the stack and inserts the second element into the first The contract storage location defined by each element also reduces the gas value by up to 200 and increases pc by one. Although there are many ways to optimize by just-in-time compilation, the basic implementation of the material chain can be implemented with hundreds of lines of code.
6 Blockchain and mining
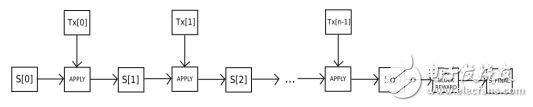
Although there are some differences, the blockchain of the thing number chain is similar to the Bitcoin blockchain in many respects. The difference between their blockchain architectures is that the blockchain block not only contains transaction records and recent status, but also contains the block number and difficulty value. The block confirmation algorithm in the material chain is as follows:
1 Check whether the previous block referenced by the block exists and is valid.
2 Check whether the timestamp of the block is greater than the previous block referenced and less than 2 minutes.
3 Check whether the block number, difficulty value, transaction root, uncle root and fuel limit (many low-level concepts specific to Ethereum) are valid.
4 Check whether the proof of work of the block is valid.
5 Assign S[0] to the STATE_ROOT of the previous block.
6 Assign TX to the transaction list of the block, there are n transactions in total. For i belonging to 0...n-1, perform a state transition S[i+1] = APPLY(S[i], TX[i]). If an error occurs in any of the conversions, or the gas spent in the program execution to this point exceeds GASLIMIT, an error is returned.
7 Use S[n] to assign value to S_FINAL and pay block rewards to miners.
8 Check if S-FINAL is the same as STATE_ROOT. If they are the same, the block is valid. Otherwise, the block is invalid.
The confirmation efficiency of the material chain is much higher than that of Bitcoin. The reason is that the state is stored in the tree structure, and each additional block only needs to change a small part of the tree structure. Therefore, generally speaking, most of the tree structure of two adjacent blocks should be the same. Therefore, when data is stored once, it can be referenced twice with a pointer (that is, a subtree hash). A tree structure called "Patricia Tree" ("Patricia Tree") can achieve this, which includes a modification to the Merkel tree concept, which not only allows nodes to be changed, but also to insert and delete nodes .
Application Generally speaking, a perfect example on the material number chain is a self-mandatory reward for solving the problem of logistics information sharing. Through the original circular calculation (annular calculate), the data sharing is made into a standardized consensus, which improves the recognition and consensus reward of the blockchain.
7 Improved Ghost Protocol
The motivation of the ghost protocol is that the current fast-confirmed block chain suffers from low security due to the high obstruction rate of the block; because the block takes a certain time (set as t) to spread to the entire network, if miner A digs out one Block Then Miner B happens to dig another block before A's block spreads to B. Miner B's block will become invalid and make no contribution to network security. In addition, there is a centralization problem: if A is a mining pool with 30% of the entire network's computing power and B has 10% of the computing power, A will face the risk of generating invalid blocks 70% of the time while B is in Obsolete blocks are generated 90% of the time. Therefore, if the invalidation rate is high, A will be more efficient simply because of a higher share of computing power. Combining these two factors, a block chain with a fast block generation rate is likely to lead to a mining pool that can actually control mining The computing power share of the process. By including waste blocks when calculating which chain is "longest", the ghost protocol solves the first problem of reducing network security; that is, not only the parent block of a block and earlier The ancestor block, the obsolete descendant blocks of the ancestor block are also added to calculate which block has the largest proof of work to support it. The thing number chain pays 87.5% of the reward for the waste blocks that contribute to the confirmation of the new block as the "uncle block". The "nephew block" that includes them in the calculation will get 12.5% ​​of the reward. However, the transaction fee is not rewarded. To the uncle block.
The material chain has implemented a simplified version of the ghost protocol that only goes down to the fifth layer. Its characteristic is that the discarded block can only be used by the second to fifth generation descendant blocks of its parents as the uncle block, rather than the descendant blocks that are more distantly related (for example, the sixth generation descendant area of ​​the parent block). Block, or the third-generation descendant block of the grandfather block) is included in the calculation. There are several reasons for this. First, the unconditional ghost protocol will bring too much complexity to calculating which uncle of a given block is legal. Second, the unconditional ghost protocol with compensation used by the thing chain deprives miners of the incentive to mine on the main chain instead of an open attacker's chain. Finally, calculations show that the five-layer ghost protocol with incentives achieves an efficiency of more than 95% even when the block generation time is 15s, and the miners with 25% of the computing power get less than 3% of the benefits from centralization.
Fees Because each transaction posted to the blockchain occupies the cost of downloading and verification, a standardized mechanism including transaction fees is needed to prevent spam transactions. The default method used by Bitcoin is purely voluntary transaction fees, relying on miners as gatekeepers and setting dynamic minimum fees. Because this method is "market-based", allowing miners and transaction senders to determine prices based on supply and demand, this method has been successfully accepted in the Bitcoin community. However, the problem with this logic is that transaction processing is not a market; although it is very attractive to interpret transaction processing as a service provided by miners to senders based on intuition, in fact, a transaction included by a miner requires every transaction in the network. The node processes, so the largest part of the cost of transaction processing is borne by the third party rather than the miner who decides whether to include the transaction. As a result, the tragedy of the commons is very likely to occur.
However, when a particular simplified hypothesis is given that is not precise enough, the loopholes in this market-based mechanism magically eliminate its influence. The argument is as follows. Assumption:
1 A transaction brings k steps and provides a reward kR to any miner who collects the transaction, where R is set by the transaction publisher, and k and R are (roughly) visible to the miner in advance.
2 The cost of processing each operation at each node is C (that is, the efficiency of all nodes is the same).
3 There are N mining nodes, each with the same computing power (that is, 1/N of the entire network's computing power).
4 There is no full node that does not mine.
When the expected reward is greater than the cost, miners are willing to mine. In this way, because the miner has a 1/N chance to process the next block, the expected profit is kR/N, and the miner’s processing cost is simply kC. In this way, when kR/N 》kC, that is, R 》NC. Miners are willing to include transactions. Note that R is the per-step fee provided by the transaction sender and is the lower limit for miners to benefit from processing transactions. NC is the cost of processing one operation on the entire network. Therefore, miners only have the incentive to include transactions where the benefits exceed the costs.
However, these assumptions have several important deviations from the actual situation:
1. Because the additional verification time delays the broadcast of the block and thus increases the chance that the block becomes a waste block, the miner who processes the transaction pays a higher cost than other verification nodes.
2. There are full nodes that do not mine.
3. In practice, the distribution of computing power may end up being extremely uneven.
4. Speculators, political enemies and lunatics who take the responsibility of destroying the network do exist, and they can set up contracts smartly so that their costs are much lower than other verification nodes.
The first point above drives the miners to include fewer transactions, and the second point increases the NC; therefore the effects of these two points at least partially cancel each other out. Points 3 and 4 are the main problems; as a solution we simply established a floating upper limit: no block can contain more operands than the long-term exponential moving average of BLK_LIMIT_FACTOR. specifically:
blk.oplimit = floor((blk.parent.oplimit * (EMAFACTOR – 1) + floor(parent.opcount* BLK_LIMIT_FACTOR)) /EMA_FACTOR) BLK_LIMIT_FACTOR and EMA_FACTOR are constants temporarily set to 65536 and 1.5, but they may change Adjust after in-depth analysis.
8 Computation and Turing completeness
It needs to be emphasized that the virtual machine of the material chain is Turing complete; this means that the virtual machine code can realize any imaginable calculation, including infinite loops. There are two ways to realize the loop in the virtual machine code of the material chain. First of all, the JUMP instruction can make the program jump back to somewhere in front of the code, and there is also the JUMP instruction that allows conditional statements such as while x << 27: x = x * 2 to achieve conditional jumps. Secondly, the contract can call other contracts, which has the potential to achieve loops through recursion. This naturally leads to a question: can a malicious user have to shut down by forcing miners and full nodes into an infinite loop? This problem arises because of a problem called the shutdown problem in computer science: in general, there is no way to know whether a given program can finish running in a limited time.
Our solution solves the problem by setting the maximum number of calculation steps to be executed for each transaction. If it exceeds, the calculation is restored to its original state but a fee is still to be paid. The message works in the same way. To show the motivation behind this scheme, consider the following example:
An attacker creates a contract that runs an infinite loop, and then sends a transaction that activates the loop to the miner. The miner will process the transaction and run the infinite loop until the fuel is exhausted. Even if the fuel runs out and the transaction stops halfway, the transaction is still correct (return to the original place) and the miner still earns the cost of each step calculated from the attacker.
An attacker creates a very long infinite loop with the intention of forcing the miner to calculate for a long time, so that several blocks have been generated before the end of the calculation, so the miner cannot record the transaction to earn fees. However, the attacker needs to issue a STARTGAS value to limit the number of executable steps, so the miner will know in advance that the calculation will consume too many steps.
An attacker sees a contract with a format such as send(A, contract.storageï¼»Aï¼½); contract.storageï¼»Aï¼½=0 and sends a contract with only enough cost to perform the first step but not enough to perform the second step Transactions (that is, withdraw cash without reducing the account balance). The contract author does not need to worry about defending against similar attacks, because if the execution is stopped in the middle, all changes will be reverted.
A financial contract works by extracting the median value of nine dedicated data publishers to minimize the risk. An attacker takes over one of the data providers, and then designs the variable address call mechanism into a changeable data provider. Run an infinite loop in an attempt to force any attempt to request funds from this contract will be aborted due to exhaustion of fuel. However, the contract can set a fuel limit in the message to prevent such problems.
The alternative to Turing complete is Turing incomplete, where the JUMP and JUMPI instructions do not exist and only one copy of each contract is allowed to exist in the call stack at a given time. In such a system, the above-mentioned fee system and the uncertainty surrounding the efficiency of our scheme may not be needed, because the cost of executing a contract will be determined by its size. In addition, Turing incompleteness is not even a big limitation. Of all the contract examples we have envisaged internally, only one needs a loop so far, and even this loop can be replaced by the repetition of 26 single-line code segments. Considering the serious troubles and limited benefits brought by Turing completeness, why not simply use a Turing incomplete language? In fact, Turing incompleteness is far from a simple solution
case. why? Please consider the following contract:
C0: call(C1); call(C1);
C1: call(C2); call(C2);
C2: call(C3); call(C3);…
C49: call(C50); call(C50);
C50: (run one step of a program and record the change in storage)
Now, send one such transaction to A, so that out of 51 transactions, we have a contract that takes 250 steps to calculate. The miner may try to maintain a maximum executable number of steps for each contract and call other recursively. The contract calculation of the contract may execute steps to detect such logic bombs in advance, but this will prohibit miners from creating contracts for other contracts (because the creation and execution of the above 26 contracts can easily be placed in a single contract). Another problem is that the address field of a message is a variable, so in general, it may not even be possible to know in advance which other contract will be called by one contract. So, in the end we have an amazing conclusion: Turing complete management is surprisingly easy, and Turing incomplete management is surprisingly difficult without the same control-then why not let the protocol Turing complete?
9 Decentralization of mining
The current purpose of the material chain is to use a mining algorithm based on a function that randomly generates a unique hash for every 1000 random numbers, using a sufficiently wide computational domain to remove the advantages of dedicated hardware. Note that every single user using their personal laptop or desktop computer can complete a certain amount of mining activities almost for free, but when the CPU usage reaches 100%, more mining will require them to pay for electricity and hardware costs. . ASIC mining companies need to pay for electricity and hardware from the first hash. Therefore, if the benefits of centralization can be kept below (E + H) /E, ordinary miners still have room for survival even if ASICs are manufactured. In addition, we plan to design the mining algorithm so that mining requires access to the entire blockchain, forcing miners to store the completed blockchain or at least be able to verify each transaction. This removes the need for centralized mining pools; although mining pools can still play the role of smoothing the randomness of revenue distribution, this function can be performed equally well by P2P mining pools without centralized control. In this way, even if most ordinary users still tend to choose light clients, increasing the number of full nodes in the network will help resist centralization.
10 Scalability
The issue of scalability is a common concern. Like Bitcoin, the IoT chain suffers from the dilemma that every transaction requires every node in the network to deal with it. Bitcoin's current blockchain size is about 20GB, growing at a rate of 1MB per hour. If the Bitcoin network processes Visa-level transactions of 2000tps, it will grow at a rate of 1MB every three seconds (1GB per hour, 8TB per year). The thing number chain may also experience a similar or even worse growth pattern, because there will be many applications on the thing number chain, not like Bitcoin, which is just a simple currency, but the whole node of the thing number chain only needs to store the state. The fact that it is not a complete blockchain history has improved the situation.
The problem with big blockchains is centralization risk. If the block chain size is increased to, for example, 100TB, the possible scenario will be that only a very small number of large businesses will run full nodes, while regular users use light SPV nodes. This will increase concerns about the risks of full node partnerships for fraudulent profit (such as changing block rewards and giving them their own BTC). Light nodes will have no way to detect this kind of fraud immediately. Of course, there may be at least an honest full node, and information about the fraud will be leaked through channels like Reddit in a few hours, but it is too late: no matter what efforts ordinary users make to abolish the blocks that have been generated , They will all encounter huge infeasible coordination problems on the same scale as launching a successful 51% attack. The material chain will use two additional strategies to cope with this problem. First of all, because of the blockchain-based mining algorithm, at least every miner is forced to become a full node, which guarantees a certain number of full nodes. Second, and more importantly, after processing each transaction, we will include the root of an intermediate state tree into the blockchain. Even if block verification is centralized, as long as there is an honest verification node, the centralization problem can be avoided by a verification protocol. If a miner publishes an incorrect block, the block is either in the wrong format or the state S[n] is wrong. Because S[0] is correct, there must be the first error state S[i] but S[i-1] is correct, the verification node will provide index i, and the processing APPLY(S[i- 1], TX[i]) -> S[i] the required subset of Patricia tree nodes. These nodes will be ordered to perform this part of the calculation to see if the generated S[i] is consistent with the previously provided value. In addition, it is more complicated that malicious miners publish incomplete blocks to attack, resulting in insufficient information to determine whether the block is correct. The solution is the challenge-response protocol: the validating node initiates a challenge to the target transaction index, and the light node that receives the challenged information will cancel the trust in the corresponding block until another miner or validator provides a subset of Patricia nodes as Correct evidence.
11 Summary
The decentralized application of the above-mentioned contract mechanism enables anyone to establish a network-wide consensus on a virtual machine to run command-line applications (fundamentally speaking), which can change a network-accessible state as its "hard drive" ". However, for most people, the command line interface used as a transaction sending mechanism lacks sufficient user-friendliness to make decentralization an attractive alternative. Finally, a complete "decentralized application" should include the underlying business logic components and the upper level graphical user interface components. The IoT Chain client is designed as a web browser, but it includes support for the "LDBC" Javascript API object, which can be used by the specific webpage seen in the client to interact with the IoT Chain. From the perspective of "traditional" web pages, these web pages are completely static content, because blockchain and other decentralized protocols will completely replace servers to process user-initiated requests. Finally, the decentralized protocol hopes to use LDBC in some way to store web pages.
12 Conclusion
The material chain protocol revolves around decentralized storage of logistics data sharing, decentralized computing, and dozens of similar concepts to establish protocols and decentralized applications, which have the potential to fundamentally improve the efficiency of the logistics industry, and by adding an economic layer for the first time Provide strong support for other P2P protocols, and eventually, there will also be a large number of applications that have nothing to do with money.
The arbitrary state transition concept implemented by the material chain protocol provides a platform with unique potential; unlike closed protocols designed for a single purpose such as data storage or finance, they are open in design, and we believe It is extremely suitable as a basic layer to serve an extremely large number of logistics industry and non-industry agreements that will appear in the coming years.
Iget Legend,Iget Legend Puffs,Iget Vape,Disposable Iget
Shenzhen Zpal Technology Co.,Ltd , https://www.zpalvapes.com