“Just in the early hours of this morning, Apple pushed an iOS 10 official update to China.
However, before you click on the upgrade, it seems that the Pangu team has completed the jailbreak of it.
The Pangu team has few core members, but it is the god of iOS jailbreak in the eyes of many people; they are China and the only hacking team in the world who publicly admits that they are capable of jailbreaking iOS 10.
What are the iOS security mechanisms?
How difficult is jailbreaking iOS?
In the days of starting to study iOS, Pangu team had encountered those difficulties?
Just released iOS 9.3.3 jailbreak tool exactly where the cow, even let Apple specifically push iOS 9.3.4 to plug the loophole?
At present, how strong is Pangu team jailbreak iOS?
In this hardened open class, we exclusively invited the founder & CEO Han Zhengguang of the Pangu Group (Benzhong Information) to listen to him open up and chat about Pangu Prison Break!

TB Han Zhengguang
Guest introduction:Han Zhengguang, flower name TB, Founder & CEO of Pangu Group (Benzhong Information).
The Pangu team is a professional security research team composed of senior security researchers. The team is best known for continuously releasing iOS perfect jailbreak tools. It is the first domestic team to independently implement Apple iOS’s perfect jailbreak, and is the first team in the world to implement a perfect jailbreak for iOS 8 and iOS 9.
Shanghai Benzhong Information Technology Co., Ltd. is an independent innovative company with Pangu team as the core. In the field of operating system security research, program automation analysis, vulnerability mining and offensive and defense research and other fields have a solid foundation. Founded in 2014, the company is dedicated to the research and product development of mobile Internet security technologies and provides professional security services and solutions for businesses and individuals.

Photo of Pangu team core members
Pangu team of big cowsLei Feng network guest channel: Pangu team's core members are relatively low-key mystery, you can tell us about the team these iOS jailbreak Daniel have?
My name is Han Zhengguang, Benzhong Information (aka Pangu Team) Founder & CEO, I was admitted to Harbin University of Technology at the age of 16, and I started my career in network security at the age of 18. I worked at security companies such as Hacker Defense and Fortinet. More than 15 years of experience in network security have been used, and basically they are working on security technology.
The Pangu team's iOS jailbreak core members include Xu Wei, Chen Xiaobo, Li Xiaojun, Wang Tielei, and Zeng Fanyu.
Xu Hao is a master of information security at Shanghai Jiaotong University.
Chen Xiaobo , who has worked in senior cyber security research positions at Venus Star Active Defense Labs, Mcafee, IntelSecurity, FireEye and other security companies;
Li Xiaojun , a master's degree from Beijing Institute of Technology, served as the assistant president of Venusen and was responsible for Venusen's active defense lab;
Wang Tielei, who has the highest degree in education here , holds a Ph.D. in computer science from Peking University and a postdoctoral fellow of Georgia Tech in the United States. The dissertation was awarded the Excellent Doctoral Dissertation by the Chinese Computer Society. It was the first domestic researcher to publish papers in the top academic conferences and journals such as IEEE S&P, NDSS, and TISSEC. Secunia Most Valuable Contributor Award in 2011;
Zeng Fanyu , who is proficient in hardware, is a well-known domestic Wenquxing and Meizu researchers. The first domestic realization of the Android system transplanted to the Meizu M8 cattle.
Apart from Zeng Fanyu's emphasis on hardware, he has basically done more than 10 years of vulnerability mining and security research.
Lei Feng network resident channel: What makes the Pangu team begin to do iOS jailbreak and security research?
In fact, for ordinary users, the jailbreaking technique is more mysterious, but for network security practitioners, jailbreaking is the offensive and defensive at the system level.
The core of the earliest Pangu is the senior researcher in the security industry at home and abroad for more than 10 years, and has always been doing research on vulnerability mining. Everyone is more interested in iOS, and they get a QQ group to study and exchange together. In early 2014, when everyone had a little bit of time, they began tossing and jailbreaking.
Lei Feng network resident channel: In addition to jailbreak, Pangu team also "toss" what?
Our company is mainly doing some research on mobile security and product development, mainly in two aspects:
The first is security services , focusing on risk assessment and security consulting of smart operating systems. Smart devices, Internet of things, and car networking systems are all basically doing.
The second is to do some security products and platforms . For example, some time ago iOS trident APT events, our iOS device security detection products can be detected without upgrading.
This test product is mainly used to detect whether the iOS system has been passed through the back door or moved. Because of the closed nature of Apple's own systems, there is no special way to detect it. Only holes can be holed, holes can be used to raise power, and the entire system can be checked for security.
In addition, there is a Janus platform that we invest a lot of manpower and energy into.
The main purpose of this platform is to find applications that comply with the rules in our application database by writing some simple detection rules. For example, the Xcode Ghost and Worm Hole events that have been previously discovered can be used to find all the existing problems through certain features. Applications.
Janus relied on our mobile application analytics engine to extract information and behavior from all the applications we collect, perform related indexing and processing, store it in our cloud database, and provide a custom rule language for retrieval. . The platform will soon be available. The main target user groups are mobile security researchers and malicious sample analysis engineers. Our internal colleagues have already rely on this platform during the trial period and found that many mobile applications with a large number of users are at high risk of risk. And malicious behavior.
How hard is it to crack iOS security?Lei Feng network (search "Lei Feng network" public concern) Channel: From your point of view, for our science and technology about iOS's security mechanism is like?
iOS system can be regarded as the best security system in the current popular operating system. According to the quotation table given by companies that have acquired security vulnerabilities from abroad, iOS has the highest vulnerability value, which can also reflect that iOS's security is higher than other systems.
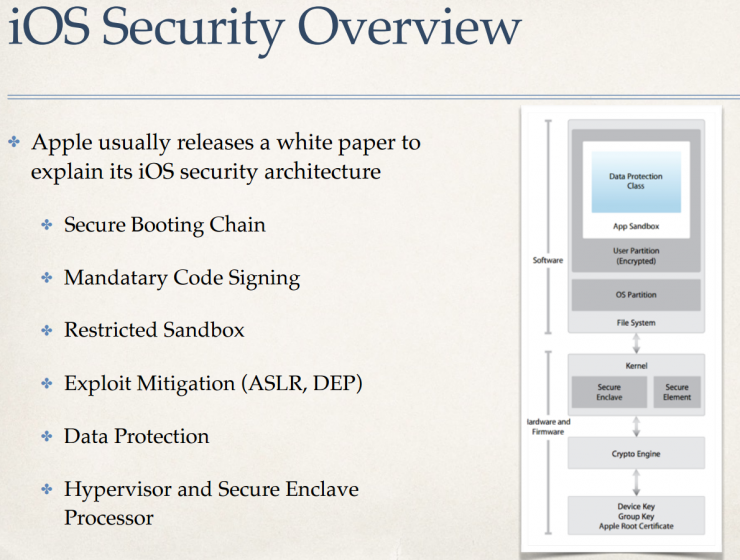
iOS security mechanism diagram
Apple's security mechanism is also increasing step by step. The difficulty of making a jailbreak early is relatively low, because the security mechanism is not perfect and it is easier to break through. The current iOS security mechanism can be mainly classified into the following aspects:
1, the system starts
Apple solidified a bootrom in the CPU. This system is read-only. This means that the system has a problem and Apple has no way to fix it. This bootrom has a built-in Apple's public key for verifying and starting Low-level boot, then Low-Level boot starts iboot, and iboot starts the kernel. Each time you start something new, the initiator checks the validity and integrity of the launched program. So if there is no bootrom/iboot level vulnerability, basically the kernel can't tamper with the kernel before the boot is complete.
2, the system update
The iOS Brush and update system is completely controlled by Apple, and users cannot downgrade at will. During the upgrade process, the iOS system will perform network verification on various parts (LLB, iBoot, kernel, system files, and baseband) of the brushed device. After the verification is passed, different signatures will be generated for each device. When the system processes the flashing device, the contents and signatures of these brushes will be checked again. If the verification fails, it is not allowed to enter the device. Requests to the server before can be replay attacks. Now that this loophole has been closed, the method used is to add a random value to each request so that replay attacks can be prevented.
This security limitation of the system update also guarantees that most users can only upgrade to a new version with a lower risk of vulnerability.
3, code signature
All built-in programs and applications on Apple's system are Apple-signed. Any third-party applications that are not signed by Apple cannot run. Even if you use Apple's code signing certificate to sign, once Apple discovers that your certificate was used for unauthorized behavior, it can also revoke it.
4, sandbox
Third-party applications running on Apple systems are all run under sandbox protection. Any program can only call the APIs allowed by the limited system. Each sandbox program can only access its own document path. This will ensure that programs in the sandbox can access and modify files of other applications and systems.
5, data protection
Apple has done a lot of things at the data protection level. All data is encrypted on the hard disk. The hard disk can't read any useful data at all. Like the technical analysis articles we wrote last time between the FBI and Apple, Apple used multiple protection measures for data stored on disk.
First of all, there is an encrypted file with a key stored in a specific area and then protected by a passcode. Only after verifying the validity of the passcode can the key used by the encrypted file be properly decrypted, and the system can correctly read the data. file. There was also the possibility of brute-force cracking passcodes on 32-bit devices. After the 64-bit device was released, the iOS system moved the brute force-proof module to the newly added security chip.
Some data that needs to be kept secret (for example, passwords of the system's wifi, mail, and vpn, and some of the login credentials of third-party applications) are stored in the keychain. The keychain data cannot be decrypted when it is obtained by other devices. It is followed by The cpu of the original device is bound. Each cpu has a different encryption key at the time of shipment. Apple does not store these keys.
6, privacy protection
Privacy protection includes randomization of Wi-Fi addresses, advocacy for enabling https, and more.
There used to be a lot of marketing tools to detect shop traffic and repeat customers. This is mainly to detect the Wi-Fi MAC address of the phone. After Apple has enabled Wi-Fi address randomization, it prevents user devices from being tracked through the Wi-Fi plane.
Enabling https is also based on the current mobile application. Although https will increase the cost of service providers, it increases the ability of communication encryption over http to prevent users and server-side communication from being sniffed by the middlemen.
7, using mitigation techniques
We generally say that there is a need to use loopholes in the jailbreak. Vulnerabilities are also divided into exploitable and unusable. The use of technology is also very different. In addition to patching the loopholes, Apple also added a lot of means to ease the use of some of the means may completely eliminate the possibility of a type of vulnerability.
For example, Apple has enabled stack overflow protection, data execution protection DEP, address randomization, kernel patch protection, and more on iOS systems. Here mainly talk about address randomization and new KPP protection in iOS9.
This is a schematic of the evolution of the iOS security mechanism that we previously demonstrated in Blackhat:

iOS security mechanism evolution diagram
Address randomization:
You can see that Apple added ASLR in 4.3. ASLR means address randomization; KASLR is added in K6, and KSLR is a kernel in KASLR.
In the past, there was an overflow vulnerability that could be used directly for writing and could be used by calling a fixed offset function. However, after the address randomization is added, the offset of the address of the function to be called before becomes unknown. Therefore, in order to determine the kernel address distribution after randomization, it is necessary to incorporate a loophole that can reveal the address. This loophole is called information disclosure vulnerability. Therefore, the difficulty of cracking this address has increased correspondingly.
KPP kernel anti-patching technology:
This technology was first enabled on iOS 9 but limited to 64-bit devices. Mainly because this technology is to rely on the newly added security chip on 64-bit devices to achieve. If this technology is still implemented through the kernel, it does not make sense at all. Because the kernel I can patch, then I can patch this function. So on the hardware, the possibility of breakthrough becomes very small.
We bypassed KPP's detection with some techniques in iOS9.
Lei Feng network resident channel: For Pangu, do jailbreak, where is the greatest difficulty?
The biggest difficulty is mainly two aspects:
1, to find loopholes to bypass various protection methods to combine a set of jailbreaks. For example: bypassing sandboxes, code execution, power escalation, information disclosure, code signing, etc. If you can't combine a set, even one type of vulnerability will not work.
2, in addition to a complete set of loopholes, but also think of all kinds of "bizarre tricks." Like our iOS 8 and iOS 9 jailbreaks are the world's first release, then iOS 8 and iOS 9 new security mechanisms and the use of mitigation mechanisms, we have to rack their brains to think of ways to get around. There is no historical experience to refer to and learn from, for example, the trick of bypassing TeamID in iOS 8.
Lei Feng network guest channel: as familiar with Android and iOS these two systems, the two systems of security mechanisms in your eyes have any difference?
In fact, many systems have some security mechanisms that are connected, such as Windows/Linux/Mac/Android/iOS. Now that Android's security mechanism is gradually moving closer to iOS, I think that Android is currently the most important lack of two, this may also be related to the positioning of Android.
The first is data protection. The data stored in Android's hard disk and memory card is completely unencrypted. Data can be obtained by disassembling the hard disk or directly reading the memory card. On Apple, you can't read useful data even if you remove the hard drive.
The second is the problem of code signing. Android's code signing mechanism feels like a decoration. At present, the main role is to check the integrity. Because everyone can generate a set of code-signed certificates themselves to sign the code, this is also the reason for the current proliferation of malware. Without a good certificate management system, the effect of this signature is not significant.
Of course there are other problems.
For example, Android has too many privileges to open . Like very private data such as SMS, any program can read it. This also led to the current proliferation of Trojans stealing SMS, it is said that a few hundred dollars can be customized for a set of Android Trojans.
Another difficulty is that fragmentation is too severe . There are too many vendors, and some vendors keep updating the system for only one year after the new machine is released. One year later, the system of this model will not be completely upgraded, and there will be no loopholes to fix it.

The Pangu team made a speech at the top hacking conference Black Hat. The picture shows Xu Wei (left) and Wang Tielei (right)
Everything about Pangu Prison BreakLei Feng Net Home Channel: Did you encounter some great difficulties when Pangu was first jailbroken?
Because the jailbreak was before foreign security researchers are doing it. Therefore, at the beginning of contact, the research data was very scarce, and the difficulties in learning and research were relatively large. And when we started our research, the iOS version was already the 7th major version, and basically the security mechanism was already on.
For example, if you are still in the era of iOS 3/4, a jailbreak in a month is not a problem. After all, one or two loopholes can achieve jailbreak.
I still remember that before the first release of jailbreak, when I was just starting to get some results, I sent screenshots and videos on Weibo. In fact, it was not completely finished at the time, but all kinds of buzz came. Basically, most people are saying that we are fraudsters.
After the first jailbreak was released, someone questioned whether the vulnerability or jailbreak was bought with money. At that time, I also wrote a microblog long text response. In addition, some foreigners are questioning whether there are backdoors for Chinese development.
However, when we released the jailbreak for the second time, these doubts basically disappeared. And since that time, we have had a good reputation for jailbreaking and security rights abroad. By now, no one has doubted our ability.
Now, we will also share some of the details of each jailbreaking technique and research at the world’s largest hacking conference, such as BlackHat, CanSecWest and others. In addition, like the second MOSSE Mobile Security Technology Summit held on July 1st this year, many foreign companies, such as Microsoft and Apple, sent people to participate.

Pangu release iOS 9.2-9.3.3 jailbreak tool
Lei Feng network resident channel: talk about the Pangu team recently released iOS 9.3.3 jailbreak tool, behind this jailbreak tool, what is unknown story?
The biggest difficulty in the jailbreak just mentioned is how to find a set of loopholes that can be matched. Most of the time the jailbreak needs 5 or so security holes. This time, we will only need one loophole to break out of 9.3.3.
Because this vulnerability has all the capabilities of information disclosure, sandbox bypass, code execution, privilege escalation loopholes, and can bypass Apple's review. Like this vulnerability is not less than the weakness of Trident, so Apple urgently released a 9.3.4 update for this vulnerability.
Lei Feng network guest channel: It is said that this jailbreak tool is better than before, you can read from the technical point of view, this jailbreak tool is perfect in what place?
In fact, the so-called perfect jailbreak and imperfect jailbreak in the past was just a translation of the foreign English “Untethered Jailbreak/Tethered Jailbreakâ€. The difference between these two jailbreaks was mainly one that did not require a computer to boot, and one that required a computer to boot.
We also want to try a new way this time, try not to modify the system files, so that users can easily switch jailbreak and normal system mode. For example, the previous perfect escape has no way to restore the factory settings. Our jailbreak this time can completely restore the factory settings. The average user will not be shut down for a long time. After restarting, you only need to click on the APP to get the jailbreak ability.
This is our pioneering work. Before the jailbreak, the equipment could not be returned to the factory. Once it was restored, it was a white apple.
Lei Feng Net Home Channel: During these years of safety research, did you compare the failure experience?
Failure is not counted, but there are many sad things. The number of loopholes that we have been bumped and sealed during these years is also relatively high.
The so-called being hit, that is, other security researchers have also found the same loophole, reported to Apple, or through other channels Apple obtained the details of the vulnerability and then patch.
The so-called closure is generally a matter of Apple's own internal discovery, or inadvertent addition of features or deletion of functions leads to loopholes that do not exist, and some of them should be regarded as exploited.
Calculating the holes that were hit and filled up, they were all good enough for several escapes. Especially after Apple launched Apple Pay, their investment in security has also increased.
But this is good for us. The higher the difficulty, the more challenging it is. Attacks and defenses have always been one, how to defend from attack, how to bypass the defense and achieve the purpose of attack from the defense. This is a process of continuous game between the two parties. It will change the system in the game. It's safer.
Pangea Team VS iOS 10Lei Feng network guest channel: For iOS 10, Pangu team has the ability to escape it?
The official version of iOS 10 is estimated to be the same as the 10.0.1 GM. This version has been used for days.
The security of iOS 10 also changes greatly. In simple terms, the attack surface is shrinking. And 10 has patched our skills to bypass KPP in 9.3.3, and the sandbox has also been enhanced.
However, we have successfully run Cydia on iOS 10.0.1 GM. Now we have a lot of details to continue research and repair. You know that jailbreaking is not just about breaking through security protection, but also trying to tie in with Cydia and CydiaSubstrate so that they can normal operation.

Chen Xiaobo Shows Jailbreak iOS 10 Beta 8 at Domestic Hacking Conference Xpwn
Lei Feng network resident channel: that is to say iOS 10 official version, should be very sure you can escape it?
At present, from the results of our research, the answer is yes.
Lei Feng Net Home Channel: Can you tell us about the interesting stories in the process of studying various beta versions of iOS 10?
When we held MOSEC on July 1, we demonstrated iOS 10 Beta 1 jailbreak.
In addition, we were prepared to demonstrate the iOS 10 beta 7 jailbreak on Xpwn, but just two days before the Xpwn, Apple suddenly released iOS 10 Beta 8. So we spent another two days preparing for the iOS 10 Beta 8 jailbreak demo.
The new security mechanism of the new system (iOS 10) has always been a challenge, because there are many unknown things, so only after trying can we know what mechanisms have been added.
However, compared to the beginning of our jailbreak, the iOS 10 difficulty of jailbreaking has decreased. After all, we already have loopholes that we can use for research. If there are no such loopholes in the hands, the new system's security research cannot be started.
This is just like we divided the general test into black box test and white box test.
Our earliest research was similar to the black box test. There was no accumulation and black eyes.
Our current test is more like a gray box test. Using the existing loopholes and experience accumulated in our hands is relatively easy.
However, it feels relaxed, but it is actually not easy. It is also relying on long-term experience to achieve the current results.

Pangu team members Xu Wei Chen Xiaobo Wang Tielei
Lei Feng Net Home Channel: From your perspective, Pangu iOS 10 jailbreak ability in what state?
Starting from iOS 8, we have always maintained the ability to continue jailbreaking the latest version of iOS. This capability is mainly used for later research. This is not a good measure of strength, but continuous jailbreaks and research are enough for us.
From a global perspective, there will not have been a lot of research on iOS security. Because the threshold for iOS is really high compared to other systems. However, as far as I know, security researchers who can do it are very good. Our goal has always been to stay at the forefront, and new security technologies can analyze the details in the first place.
Lei Feng network guest channel: Next is a heavy question, will Pangu iOS 10 jailbreak tool?
This is a headache problem. According to our past practice, we are never spoiled before release. The main reason is that I don't know when it will be released. This depends on many factors. We must consider the results before we can do so.
These factors include:
How is the stability of Apple's system version?
How much is the audience?
Does the reserve we have in hand allow us to open the loophole?
. . .
For example: General iOS 10.0.1 This Pangu certainly will not publish jailbreak tools, because this is the first version, stability is not enough.
In addition, for example, many users of the iPhone 7 have not yet gotten their hands. We made no sense.
If we find another set of loopholes in our hands, it may also prompt us to release jailbreaking tools.
Lei Feng network home channel: rivers and lakes upload said that Pangu in the maintenance of two or more sets of escape loopholes, will release jailbreak tool, is that right? How many sets of jailbreak iOS 10 vulnerabilities exist in Pangu? Is it convenient to disclose it?
(Two sets of loopholes) This is also a standard measure. After all, if you keep a set in your hand, the possibility of being sealed and bumped will be greater, and the follow-up study will also be affected. Therefore, there are more than two sets of heart will be more emboldened.
At present, there are two sets of jailbreak loops in our hands.

Pangu (Benzhong) R & D equipment safety testing products
What is Pangu’s big move?Lei Feng network resident channel: Pangu is "a word does not fit the zoom" style, then Pangu in the future will put what big move it?
Our security research team is not too small. iOS research is just one piece, and the security of many operating systems is our research direction. For example, our laboratory's Wenguanxing reported to Adobe Adobe dozens of Flash vulnerabilities this year. In addition, we will continue to train newcomers internally. After all, there are few security researchers who can do this kind of underlying system at present.
Janus was a super big move of our company. We have invested a large number of security researchers and developers to make the analysis platform for this mobile system application. We integrate our capabilities for mobile application security research with some automated analysis tools, combined with big data platforms, for use by security researchers and malicious program analysts.
Give two examples:
1. If a security researcher finds a bug in a mobile application, by regularizing the characteristics of the vulnerability and then searching on our platform, we can quickly list all applications that meet the characteristics of the vulnerability. come out.
2. If a malicious sample analyst finds a malicious sample, he can also regularize the malicious behavior and then retrieve it so that all malicious programs can be listed.
This also incorporates some third-party threat intelligence and integrates with our system for correlation analysis. This can significantly increase the security of the mobile application market and reduce the spread of malicious programs. We will also work with operators and national authorities to strive to maximize the protection of user privacy and data.
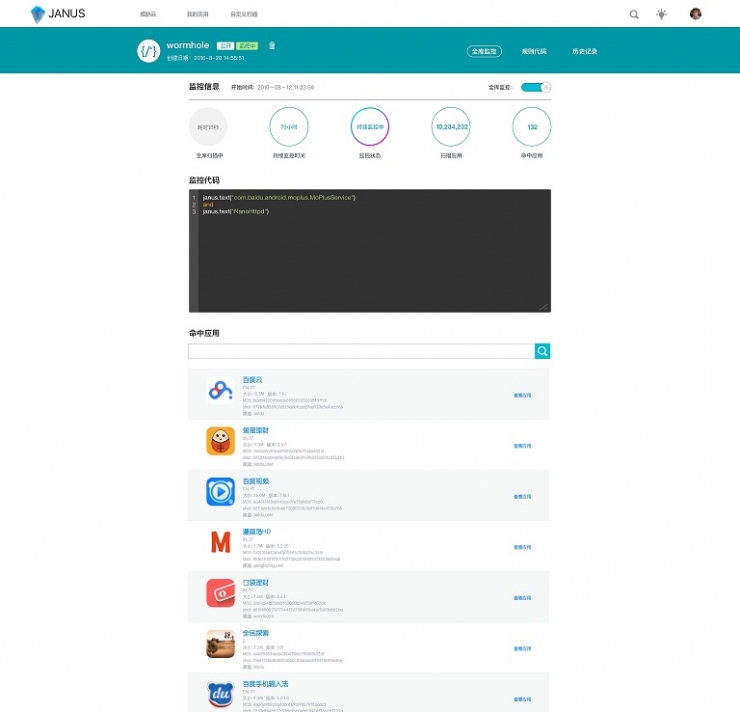
Janus Platform Work Interface
Wonderful question and answerQ: It is getting easier to use the Pangu Prison Break tool now. After an ordinary user escapes from the prison, the mobile phone may be in an unsafe state. What advice would you give?
This is the price of freedom and freedom. For example, any software on the Windows platform can be installed, and there are many viruses, but it can't be used for no reason.
Prison breaks are intended to achieve freedom. First of all, there is certainly a reduction in safety. This is undoubtedly true. But not all security mechanisms will be destroyed. Strictly speaking, jailbreaking just cancels the validation of Apple's code signatures. So if the average user wants to escape, but also want to be safe, then when installing third-party plug-ins or software, try to choose a trusted source installation.
In addition, the sandboxing mechanism of iOS is not undermined. Applications installed in normal stores still cannot get system privileges. Only the plug-ins and applications you install through Cydia will be able to do the damage. This depends on experience. Just like my Windows never installed any anti-virus software, but basically it would not be a virus.
Q: Will the current jailbreak affect the security of Apple Pay?
Apple's applepay can be used offline, all information is stored in a separate secure hardware. The security of Apple Pay is provided by the underlying hardware. This system does not interfere. Even if you escape from prison, you still have no way to get your credit card information.
Q: How is the core idiom of the jailbreak team divided? For example, who discovered the loophole and wrote Poc to write Exploit. Is there a clear division of labor? And Pangu are all promoting the 5 big cows, no newcomers have not found iOS loopholes? Still want to hide?
This depends on the individual's focus and experience. Some colleagues are more familiar with hardware. Some colleagues use well-written, some are looking for loopholes and experience, and are divided according to the direction of focus. Colleagues who are likely to find loopholes are not good at writing. , then he can write poc on it, the other to experienced people to do it.
Some of the newcomers are responsible for other directions. For example, Windows/Flash, etc., the information they report to the official will also carry personal information, and our external publicity will not hide them. For example, we have a new colleague to go to BlackHat Europe to speak in a while.
Q: If you want to become a big team of Pangu team, how should you work hard?
The iOS security research we have done requires more knowledge, including ARM, ARM64, and the underlying operating system, and some other security research experience accumulated on other platforms.
All involved in binary research, the threshold will not be low, and the time cost is also high. This must be of interest, but also tolerate sex. It is possible that there will be no results for a year.
Many people enter the industry through tools written by others. If you want to go deeper, you must study the principles of the lower level. If you only use tools blindly and cannot change your thinking, then the person himself is not suitable for further development in this industry.
Of course, if some students are interested in Pangu and Benzhong and want to be a member of us, they can also log on to our website.
Http://pwnzen.com

This concludes this speech. More big cows speak, please continue to focus on "home channel".
House guest Letshome
Lei Feng network reported the public number.
Focus on pioneering technology and tell the story behind hackers.
PDU Aluminum German Power Strips
Pdu Aluminum Power Strips For Computers,Pdu Aluminum Power Strips For Cruise Ships,Pdu Aluminum Power Strips For Outdoor,Pdu Aluminum Power Strips For Outdoor Use
Yang Guang Auli Electronic Appliances Co., Ltd. , https://www.ygpowerstrips.com